Understanding DNS Phishing
What’s DNS?
Let’s start with the fundamentals. DNS (Domain Name System) is basically the Internet’s phonebook. You give it a hostname, and it gives you back an IP address. Simple as that.
Without DNS, you’d have to memorize the IP address for every single site or service you connect to. Considering there are hundreds of millions of websites out there, that’s obviously not happening. DNS handles the mapping so you don’t have to, and thankfully, neither do your users.
What is DNS phishing?
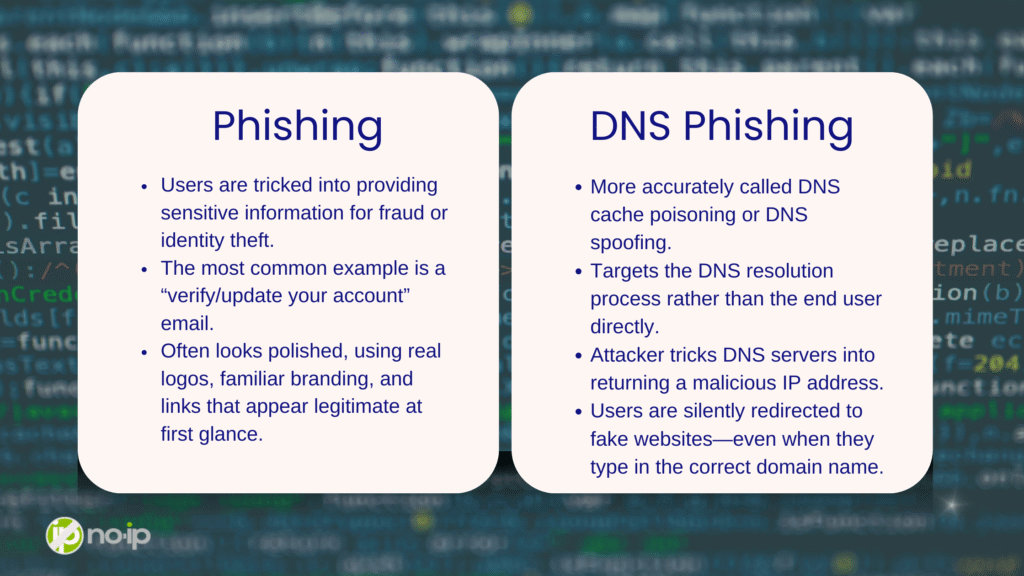
Phishing is when someone sends a message pretending to be a legitimate company in order to trick the recipient into handing over sensitive information that can be used for fraud or identity theft.
The most common version you’ll see is the “please verify/update your account” email. It usually looks polished: real logos, familiar branding, and links that appear to point to the company’s actual site (at least at a glance). To an end user, it can look completely legit.
The payload is simple: they ask for credentials. Username, password, MFA codes, sometimes even SSNs or other sensitive data. As sys admins, we know the rule: no legitimate company or financial institution is going to ask for passwords or highly sensitive info over email. If an email is asking for that,
So what is DNS phishing? DNS phishing is more commonly referred to as DNS cache poisoning, or DNS spoofing, and To put it simply, they redirect users to fake sites. Where phishing is the malicious act of tricking the user, DNS cache poisoning is the malicious act of tricking the network servers.
Why DNS is a weak link
Instead of thinking of DNS as weak, think of it as vulnerable. In its creation, DNS was not constructed with security in mind. It is simply the foundation for assigning hostnames to IP addresses. Therefore, the ramifications of malicious intent with DNS can be incredibly dire and impact millions of users. However, there are safeguards and tools in place to prevent these types of attacks from happening.
How Attackers Use DNS to Phish: Techniques & Examples
So how does DNS cache poisoning, or spoofing, work exactly? It is a technique in which an attacker inserts fraudulent DNS data into a resolver’s cache. When that happens, subsequent DNS queries return the wrong IP address, and users are silently redirected to unintended (and often malicious) destinations.
At the root, IP addresses function as the “phone numbers” of the internet. DNS resolvers act as distributed directories, caching those mappings so clients don’t have to perform a full lookup every time. Why is this important? This step is critical for performance and scalability, but it also exposes a vulnerability: If a resolver stores incorrect information, it will continue handing out that bad data until the TTL expires or the cache is cleared. Importantly, the legitimate domain and its authoritative IP address remain unchanged, but the issue exists in the poisoned cache, not at the source.
So how does poisoning occur?
In a typical attack, the attacker attempts to impersonate an authoritative DNS nameserver. They trigger a lookup request to the target resolver and then race to send a forged response before the legitimate nameserver replies. If the resolver accepts the malicious response, it caches the falsified record and begins serving it to clients.
This attack vector is historically feasible for two main reasons:
- DNS primarily uses UDP, which is connectionless and does not provide built-in session validation like TCP.
- Traditional DNS lacks strong verification mechanisms, meaning resolvers must rely on transaction IDs and source port randomization to validate responses: controls that can be predicted or brute-forced under certain conditions.
This results in users believe they’re connecting to trusted services while actually communicating with attacker-controlled infrastructure.
DNS caching improves performance, but without safeguards such as DNSSEC validation, proper source port randomization, and hardened resolver configurations, it can also introduce systemic risk. Understanding how poisoning works is the first step toward mitigating it.
Attacks Under the Radar: Domain Shadowing
Domain shadowing is a more covert variant of DNS hijacking, designed specifically to fly under the radar.
Unlike traditional hijacking, where DNS records are visibly altered or redirected, domain shadowing is about subtlety. The attacker doesn’t disrupt existing services. Instead, they quietly create new, malicious subdomains under a legitimately registered (but compromised) domain.
Here’s how it typically works:
First, the attacker gains access to the domain’s management interface, often through stolen registrar credentials or phishing. Rather than modifying or deleting existing DNS records, they add new subdomains that point to infrastructure they control.
Second, and this is what makes the technique effective, they leave all legitimate DNS records untouched. The organization’s website continues to load normally. Email keeps flowing. APIs and other services remain operational. From the domain owner’s perspective, everything appears business as usual.
Because existing services function normally, there’s no immediate trigger for investigation. Routine monitoring may not flag the new subdomains if DNS changes aren’t closely audited. As a result, malicious entries can persist for extended periods.
For attackers, the payoff is significant. They gain the ability to generate large numbers of subdomains, often automatically, under a domain that already has an established, trusted reputation. These subdomains inherit the parent domain’s credibility, making them more likely to bypass reputation-based filtering, email security controls, and web filtering solutions.
DNS integrity isn’t just about protecting primary records. It also requires:
- Strong registrar account security (MFA is non-negotiable)
- Monitoring and alerting for DNS record changes
- Periodic audits of all subdomains
- Automated detection of anomalous subdomain creation
And this isn’t limited to low-profile targets. We routinely see campaigns aimed at telecommunications providers, media organizations, ISPs, and IT service providers. Why? Because compromising infrastructure-level organizations offers scale. If you control DNS at a service provider level, you don’t just redirect one user– you can potentially redirect thousands or millions.
Massive Attack: DNS Hijacking
In many cases, DNS hijacking is financially motivated. Attackers aim to capture login credentials, session tokens, personal data, or payment information. But it’s not always about money. Some campaigns are state-sponsored, using DNS manipulation as a surveillance tool. By redirecting traffic or selectively filtering content, threat actors can collect political intelligence, monitor dissidents, or shape access to information, all without the end user realizing it.
For businesses, the impact can be severe:
- Data breaches resulting from credential harvesting
- Direct financial losses
- Service disruption
- Long-term reputational damage and erosion of customer trust
The cryptocurrency sector is particularly vulnerable. DNS hijacking campaigns frequently target crypto exchanges, wallet providers, and DeFi platforms. By redirecting users to realistic phishing clones, attackers can steal private keys or login credentials. And because cryptocurrency transactions are irreversible, once funds are transferred, recovery is often impossible. That makes DNS-level attacks especially attractive to financially motivated groups.
DNS hijacking works because users trust the address bar. Protecting that trust starts with hardening the systems that translate names into destinations.
Hidden Risks & Signs You Might Be Under Attack
At a high level, subdomain hijacking happens when someone takes control of a legitimate subdomain because of a dangling DNS record. This usually occurs when a DNS entry (like a CNAME) still points to a third-party service that your team no longer uses. Maybe a marketing microsite was decommissioned, a SaaS tool was retired, or a cloud resource was deleted, but the DNS record was left behind. If that external service is no longer claimed by your organization, an attacker can register or re-create the same service on their end. Because your DNS still points to it, they effectively gain control of that subdomain under your trusted domain.
When DNS hijacking is in play, the signs aren’t always dramatic, but they’re usually noticeable if you know what to look for.
One of the first clues is unusual slowness when loading websites. Pages that normally open instantly may lag, stall, or partially load. That’s often because your traffic is being redirected through infrastructure it was never meant to pass through.
Another red flag is unexpected pop-up ads, especially on sites that typically don’t serve them. If a trusted website suddenly looks like a low-quality streaming site from 2008, something behind the scenes may be rewriting or rerouting your traffic.
You might also see scareware-style pop-ups claiming your device is infected with malware and urging you to download a fix immediately. These messages are designed to create panic and push you into clicking or installing something malicious.
Individually, these symptoms might seem like minor annoyances. But together, they can point to DNS manipulation where requests meant for legitimate destinations are quietly being sent somewhere else.
DNS Security Best Practices to Prevent Phishing
The key takeaway? When normal browsing behavior changes without a clear reason, it’s worth investigating. DNS issues often show up as “weird internet behavior” long before anyone officially labels it an incident. Luckily, there are best practices that help prevent phishing of all types.
Restricting access to your DNS account is more than just being protective over your login credentials. When you need to protect a network, Access Control Lists (ACLs) are some of your first lines of defense. ACLs act like digital bouncers that determine who gets in and who’s denied access. Commonly used in firewalls and routers, they allow or restrict traffic based on factors like the source or destination IP addresses, as well as protocols and ports.
Utilizing a DNS provider that has a proven track record of service, you can rest assured knowing that your DNS is in the right hands. Using a trusted DNS provider is the best first step toward DNS reliability.
DNSSEC is one of the few controls that strengthen security at the infrastructure layer itself—the layer most users never see, rarely question, and often trust implicitly. By adding cryptographic validation to DNS responses, DNSSEC helps ensure that the answers your systems receive are legitimate and haven’t been tampered with along the way. It’s a foundational improvement, not a surface-level fix.
Always remember that DNS must be handled as a security asset, not just a networking asset.
How No-IP Can Help: Your Action Plan for DNS Security
At No-IP, managed DNS is built around performance and reliability. Our globally distributed Anycast network is designed to minimize downtime and keep queries resolving quickly, no matter where your users are located. Security is layered in as well, with protections like SSL and two-factor authentication to help safeguard accounts and reduce the risk of unauthorized access. And as your environment grows, the platform scales with you without forcing a redesign of your infrastructure.
Whether you’re setting up secure remote access to a home lab or running production systems that demand expert-backed infrastructure, there’s a solution to fit your needs. Our Dynamic DNS (DDNS) service automatically updates your DNS records when your IP address changes, so you’re not stuck chasing connectivity issues. By keeping your DNS records current, you maintain consistent, reliable access to your network or domain.
If you’re looking to strengthen your DNS foundation while keeping management simple, it may be time to explore what No-IP can offer.
Protect Your DNS. Protect Your Brand.
When browsing behavior gets “weird,” investigate early: DNS issues often surface before a phishing campaign is formally detected. Lock down access with strong ACLs, choose a DNS provider with a solid reliability and security track record, and enable security tools to add cryptographic validation at the infrastructure layer. Those foundational steps dramatically reduce your phishing exposure.
If you’re looking to simplify that process, No-IP offers managed DNS built for performance, resilience, and scale. With a global Anycast network, built-in security features like SSL and 2FA, and Dynamic DNS to keep records updated automatically, it’s designed to help you maintain secure, reliable resolution without adding operational overhead.